Companies hold a significant amount of data within their normal business cycle which includes company and customer data, and employee personal information. All of which requires a certain level of data handling and protection to ensure there is no fraud or theft from a third party or internal person.
These measures are especially true for health care and health care insurance organizations, where common data like names, addresses, emails, phone numbers, and credit card details need protection. Safeguarding this data inhibits the occurrence of breach.
What is HIPAA?
HIPAA stands for the Health Insurance Portability and Accountability Act. HIPAA is a United States federal law enacted by the 104th Congress and signed into law by President Bill Clinton in 1996 which mandates the creation of regulatory standards to protect Personal Health Information (PHI) from being divulged without the owner’s knowledge. Consent is required from the patient before the covered entity (healthcare providers and healthcare businesses) can disclose any protected information to anyone other than a patient and the patient’s authorized representative.
What is HIPAA Compliance?
HIPAA compliance is a discipline that health care organizations should abide by to protect the privacy and security of individuals’ protected health information. However, defining it is easier than doing it.
HIPAA is not just a simple checklist but an extensive approach to protecting the PHI, thereby protecting the patients themselves.
When you say you’re compliant with HIPAA, it means you have satisfied all the key elements of HIPAA, particularly the Privacy Rule and Security Rule. Read more below to know the specific things you need to comply with HIPAA.
What is PHI?
PHI or protected health information is an actual piece of specific information relevant to the person, which is used and disclosed during the person’s diagnosis or treatment. According to the Department of Health and Human Services (HHS), there are 18 types of information considered as PHI:
- Name
- Address
- Any date where the individual is directly linked to the person (e.g., birthday, admission date, date of death, etc.)
- Social Security number
- Medical record number
- Phone number
- Fax number
- Email address
- Health plan beneficiary number
- Account number
- Vehicle identification numbers (e.g. serial number, license number, etc.)
- Certificate or license number
- Web URLs
- IP address
- Biometrics (fingerprints and voice prints)
- Photos
- Any unique identifiers in the form of numbers, codes, or characteristics
What is ePHI?
The ePHI, on the other hand, is simply PHI in electronic format. All the mentioned 18 PHI items that are produced, saved, and transmitted in electronic form, belong to ePHI.
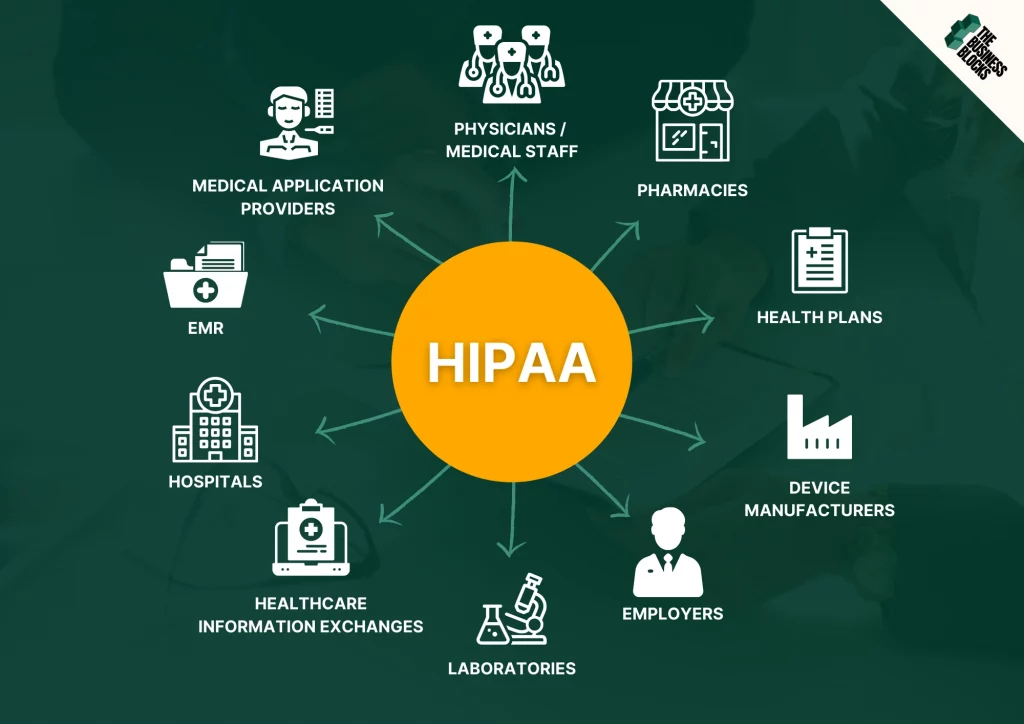
What industries and countries require it?
There are two types of healthcare organizations that need to adhere to HIPAA compliance: covered entities and business associates.
Covered entities
Covered entities are corporations or organizations handling ePHI.
- Healthcare providers include medical professions like doctors, dentists, psychologists, and chiropractors, and medical organizations like hospitals, clinics, pharmacies, and nursing homes.
- Health plans include HMOs, health insurance companies, company health plans, Medicaid, and Medicare. Even schools and employers who handle PHI still fall under this category.
- Healthcare clearinghouses receive information from a healthcare entity, manages the data in a standard template, then relay the data to another healthcare entity.
Business associates
Business associates are vendors or third-party entities who are granted access to PHI. In other words, they use or disclose PHI on behalf of covered entities.
Examples of business associates are the following:
- Software companies or firms that are exposed to or use PHI
- Medical equipment businesses handling equipment that holds PHI
- Companies that are into documentation storage or shredding
- Consultants that conduct audits, perform coding reviews, etc.
- Lawyers
- External auditors or accountants
- Professional translator services
- Accreditation agencies
- e-prescription services
- Medical transcriptionists
So, does your business need HIPAA compliance? Well, if you handle protected health information, then you must comply with HIPAA, else you’ll be charged with violation penalties.
What is the governing body that creates/requires HIPAA compliance?
The U.S. Department of Health and Human Services or HHS, particularly the Office for Civil Rights, governs the HIPAA compliance of the healthcare organization. The aim of the department is to foster the well-being of individuals, which also means protecting the privacy of their data.
You can access full information about HIPAA on their website, as well as read the latest HIPAA updates, and file complaints.
Why is it important for security and your business?
Ultimately, the main benefactors of HIPAA compliance are the patients. When you protect their PHI, you will also be protecting them from possible dangers that may arise when this data is misused by other parties. Your health records are loaded with personnel information that can be linked to personnel data.
HIPAA has established rules requiring businesses to control the individuals or organizations who can access the data. This restriction sets the qualification on who can view or share the information. Furthermore, HIPAA gives the patients control over who can access their information and to whom it can be shared.
HIPAA is highly beneficial for patients who want to take part in monitoring their healthcare and want to have copies of their PHI. Though healthcare organizations are meticulous in managing data protection, committing errors is not impossible. If patients can have their copies, they can also check for possible errors.
| Before publishing the results of clinical trials, physicians must obtain HIPAA authorization. Before including materials involving photos and rare diseases, they are reviewed meticulously. Source: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC2793939/x |
Aside from this, it will also be advantageous for employees if they seek treatment from other healthcare providers. Obtaining copies of their PHI helps the information to be passed on easily without repeating any tests. Moreover, the healthcare providers will have a historical record of the patient’s health, guiding them in making decisions.
What are the rules of HIPAA?
The strength of your organization’s HIPAA compliance lies in your knowledge of the main HIPAA rules. Having a good grasp of HIPAA rules and their latest updates will result in error-free documentations.
Breach Notification Rule
The Breach Notification Rule establishes the standard the patient’s record is compromised because of a data breach. There are two kinds of breaches: Minor and Meaningful.
Regardless of the breach’s scale, all organizations, whether business associates or covered entities, must immediately report it to HHS. The format and procedure of reporting depend on the nature of the breach that occurred.
Privacy Rule
The HIPAA Privacy Rule establishes the standards for protecting the individual’s records and personal health information. This rule mandates applying precautionary measures to protect the privacy of personal health information and sets appropriate conditions for disclosure of such information without the individual’s consent.
The first proposal of the Privacy Rule was submitted in 1999, finalized in 2000, and has been continually modified throughout the years until 2020.
Security Rule
The HIPAA Security Rule contains the standards that aim to protect electronic personal health information or ePHI. This rule dictates the security requirements of the organization so that the ePHI’s of the employees are safeguarded.
The Security Rule demands that covered entities should maintain proper technical, administrative, and physical safeguards.
- Preserve the integrity, availability, and confidentiality of e-PHI.
- Determine and protect against possible threats to the security or integrity of the PHI;
- Protect against possible anticipated, unlawful uses or disclosures; and
- Ensure workforce compliance
Transactions Rule
The HIPAA Transactions Rule enforces the standardization of electronic formats used in handling PHI. With the advantage of electronic data interchange (EDI), information is seamlessly moved from one computer to the other, without any human intervention. This results in more efficient transactions such as claims submission, data reporting, and eligibility checking.
Identifiers Rule
For covered entities using HIPAA financial and administrative transactions, HIPAA has different identifiers. It requires health care providers to have a National Provider Identifier Number or NPI, which will identify them on their administrative actions.
Enforcement Rule
The HIPAA Enforcement Rule establishes the penalties for violations committed by business associates or covered entities. The regulations in this rule will help HHS regulators in identifying specific liabilities and computing fines for healthcare providers that deviate from HIPAA rules.
What are the different HIPAA standards?
To clearly define the safeguards for data protection, the HIPAA established rules and standards according to the following sections:
- Administrative Safeguards
- Physical Safeguards
- Technical Safeguards

Physical Safeguards
The organization must ensure that covered entities have limited physical access to its facilities while also ensuring to allow authorized access. The covered entity must implement protocols in the proper use and access to electronic media and workstations. They must also have policies in handling electronic media so that the ePHI is properly safeguarded.
Administrative Safeguards
Administrative Safeguards are under the HIPAA Security Rule and provide guidelines on internal organization, procedures, and appropriate security measures to protect PHI. Here, you will assess the security controls you implemented and give a thorough analysis.
Examples of administrative safeguards include staff training programs, policies and procedures, and auditing and monitoring.
Technical Safeguards
According to HIPAA, the Technical Safeguards address controls in data access, data at rest (data stored in a device), and data in motion (data transmitted to another device). The covered entity must implement policies and procedures that can establish access restrictions to those who have been granted rights only.
Users must have unique identification (ID) used to identify and track the user’s activities while accessing PHI. To protect the data during a period of computer inactivity, an automatic log-off feature must be implemented.
What are the common violations?
Violating HIPAA standards is a serious matter. The penalty fines can be very expensive, depending on the violation committed. Most HIPAA violations are done internally, not externally like hacking.
Listed below are the most common HIPAA violations:
- Filing Unsecured Records
Documents with PHI must be kept in secure locations. For physical files, they should be locked in desks or cabinet desks. For digital files, ensure that the files have passwords
- Unencrypted Data – Encrypting the data will add another layer of security. In the event of a stolen device containing PHI, you can protect the data.
- Lack of Employee Education – Wrong actions are a result of the lack of education. HIPAA law requires HIPAA training for employees that come in contact with PHI.
- Loss of Device – A loss or theft can result when you don’t place the device in a secure location.
- Gossiping – When co-workers chit-chat with one another, there’s a possibility of sharing information. The PHI must not be brought up during conversations or discussions.
- Employee Integrity – This will help ensure that confidential information will not be compromised.
- Records Disposal Inefficiency – Once records are way beyond their retention period, staff members tend to throw them away. They must be reminded to apply proper disposal of PHI records. When documents are carrying PHI like social security numbers, they must be shredded. In the case of digital documents, they should be deleted permanently from the hard drive. Double-check with recycle bin and delete the file just to be sure.
- Unauthorized release of information – This occurs when the media releases PHI of public figures and celebrities.
- Hacking and Cyberattacks – Although it’s less likely, it’s still a possibility. Hackers could infiltrate the system and use the ePHI for malicious purposes. A good and updated antivirus software is the key here.
Elements of an Effective HIPAA Compliance Program
- Implementing policies and procedures.
Policies and procedures must be written in a manner that can be easily understood by the people. The more comprehensible the policies are, the easier it will be to comply.
2. Assigning a compliance officer and committee.
There should be a team to oversee the whole endeavor of HIPAA compliance. The compliance officer and committee spearhead the prevention, detection, and correction of any non-compliance.
3. Conducting training and development
New personnel must be specially trained with HIPAA compliance and be given regular refresher training. Keep in step with HIPAA updates by attending conferences, reading publications, and professional networking.
4. Developing efficient communication lines.
Having a seamless communication line is a great way to report any potential non-compliance
5. Conducting internal audits.
Do not wait for the big day. Anticipate all issues by auditing your whole organization and comparing it with the required HIPAA standards.
Got any questions? We’re happy to help! Click here to send in your questions.